A Comprehensive Guide to Reverse Engineering Android Apps
Written on
Chapter 1: Introduction to Reverse Engineering
In this guide, we will explore a straightforward method for decompiling Android applications, whether they are installed on your device or downloaded externally. It’s important to note that this technique is intended solely for educational purposes to gain insight into app development. I do not take responsibility for how you use this knowledge.
Reverse Engineering Explained
To put it simply, reverse engineering involves taking the executable code of a system and deriving its source code. This process can sometimes allow for modifications and recompilation, a practice often exploited by hackers to bypass security measures in software.
For compiled languages such as C or hybrid languages like Java and C#, reverse engineering entails reading binary code from files like CLASS, DLL, or EXE and translating it back into a human-readable format.
The first step in reverse engineering an Android application is obtaining the .APK file of the app you're interested in analyzing. If you downloaded this app from the internet (outside of Google Play), you can skip the next two sections. If you acquired it from Google Play, continue reading as these steps are essential.
Section 1.1: Gaining Administrator Access (Rooting)
By default, Android restricts user access to its operating system resources, including installed applications. To enhance security, Google Play limits app downloads to mobile devices only.
However, "rooting" your device can remove these security restrictions, granting you superuser access. Rooting allows you to view and manage installed applications more freely.
I recommend using KingoRoot for this process. While I have had success with it, there are no guarantees it will work for your device. Additionally, rooting voids your factory warranty, so proceed with caution.
Once you've installed KingoRoot, enable USB Debugging on your Android device. Launch KingoRoot as an administrator and click the designated button to root your device.
Section 1.2: Installing Apps on Your Device
Now that you have admin privileges, you can download Titanium Backup from Google Play. This tool allows you to back up other apps installed on your device. Note that Titanium Backup requires a rooted phone to operate effectively.
To use Titanium Backup, disconnect your phone from your computer. Start the app, select the “Backup/Restore” option, and choose the app you wish to back up.
After backing up, reconnect your smartphone to your PC, navigate to your SD card, and copy the TitaniumBackup folder containing your app backup.
Chapter 2: Reverse Engineering the APK
Once you have the APK file, rename its extension to .ZIP and extract its contents. The APK is essentially a zipped folder that contains the entire directory structure of the application, including static files, resources, and Java classes compiled into a file named classes.dex.
DEX is the executable file type understood by Android’s Dalvik virtual machine. To convert it into a traditional Java executable (.JAR), I recommend using Dex2Jar, an open-source tool available on GitHub. Simply copy classes.dex to the same directory as Dex2Jar, open the command prompt, navigate to the Dex2Jar folder, and execute the command:
dex2jar.bat classes.dex
This will produce a classes_dex2jar.jar file. You can then rename this file to .ZIP and extract it to access the project directory structure in a Java-compatible format.
However, the .class files generated are still in bytecode format and not human-readable. To convert these to plain text .JAVA files, you can use JD-GUI, which allows you to view the original source code.
The first video, "Reverse-Engineering an Android app," provides a visual guide to the decompilation process.
Section 2.1: Accessing an App’s SQLite Database
If the application includes a database, you might be interested in retrieving it for a deeper understanding of the app's functionality or for data recovery purposes. Titanium Backup also saves the application’s database in the backup folder.
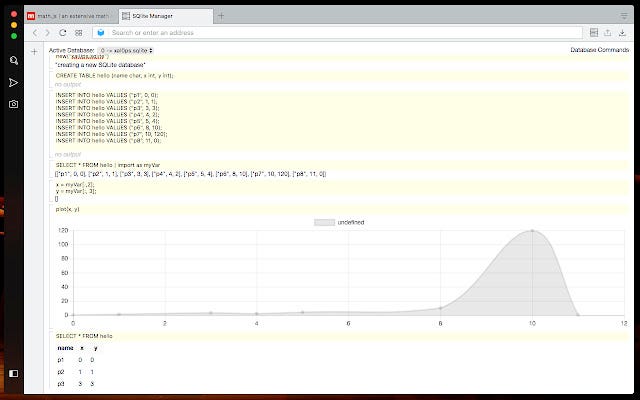
Inside the backup, look for a file with the .db extension, which is the SQLite database used by the app. To open this file, I recommend SQLite Manager, a Chrome extension that allows you to view .db files and execute queries on the database.
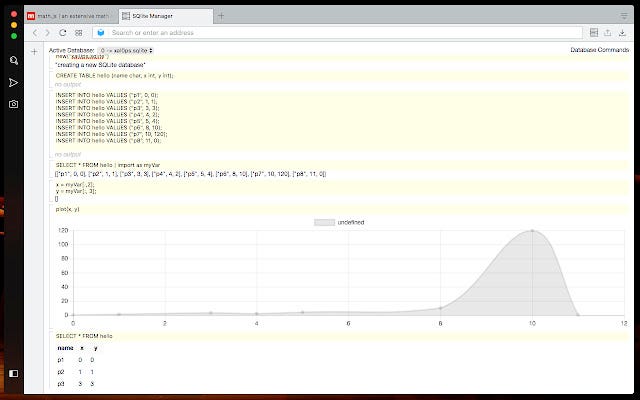
Conclusion
While the reverse engineering process may seem lengthy, it is quite straightforward with the right tools. By utilizing a series of small applications, you can effectively access the source code and data of any Android application. This process is well-documented online and is made possible by the architecture of Java and Android, which supports decompilation.
The second video, "How to reverse engineer android phone APK," complements this guide by outlining additional techniques for APK analysis.